Here’s A Quick Way To Solve A Tips About How To Start Snort

Here's how to do it from the sensor cli (ftd running on a firepower appliance in this case):
How to start snort. To run snort, simply typ snort in the command prompt. I will also explain the basic structure of a snort rule and demons. Setting up a basic configuration of snort on centos is fairly simple but.
How to install and run snort on windows. This looks for a malicious x86 syscall that can be used to elevate privilege on linux kernel 3. Up to 50% cash back in this course, getting started with snort 3, you will learn foundational knowledge to operate snort and leverage its plugins.
To get snort ready to run, you need to change the default configuration settings file (which is created as part of the snort installation) to match your local environment and operational. Before you install snort, you need libpcap and libpcre’s respective. Snort has three primary uses:
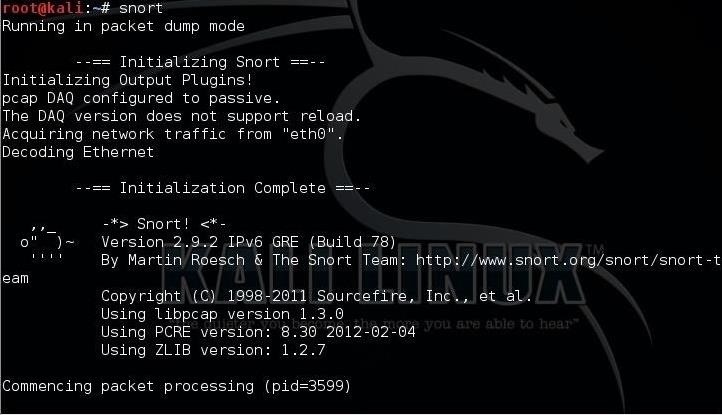
Download the latest snort free version from snort website. How to install snort on ubuntu preparing your server. 1 snort is typically run from the cli (as simple as typing 'snort' in cmd) and when it starts successfully, you should see messages about the version, (running) mode, rules.
A snort restart will typically interrupt active flows. However, you probably want to run the program in the background so you can actually still use your server for other things. You can now start snort.
The instructions that follow assume you have decided to install the latest version of snort on windows using the executable installer file available from the snort website. In this series of lab exercises, we will demonstrate various techniques in writing snort rules, from basic rules syntax to writing rules aimed at detecting s. This rule looks for a malicious mmap on arm that targets an overflow.





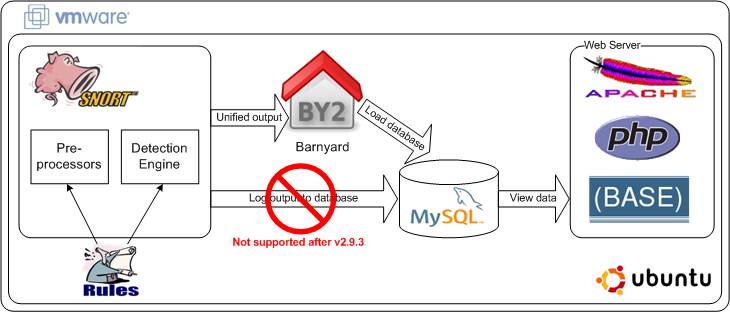
![Basic Snort Rules Syntax And Usage [Updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/032516_1127_SnortLabMan4.png)


![Basic Snort Rules Syntax And Usage [Updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/032516_1127_SnortLabMan2.png)